Understanding File Metadata
From Site Features
From Site Features
Entries in Packet Storm provide a set of metadata to better enable our users. The below key explains each line of data, why it's included, and how it can be used.
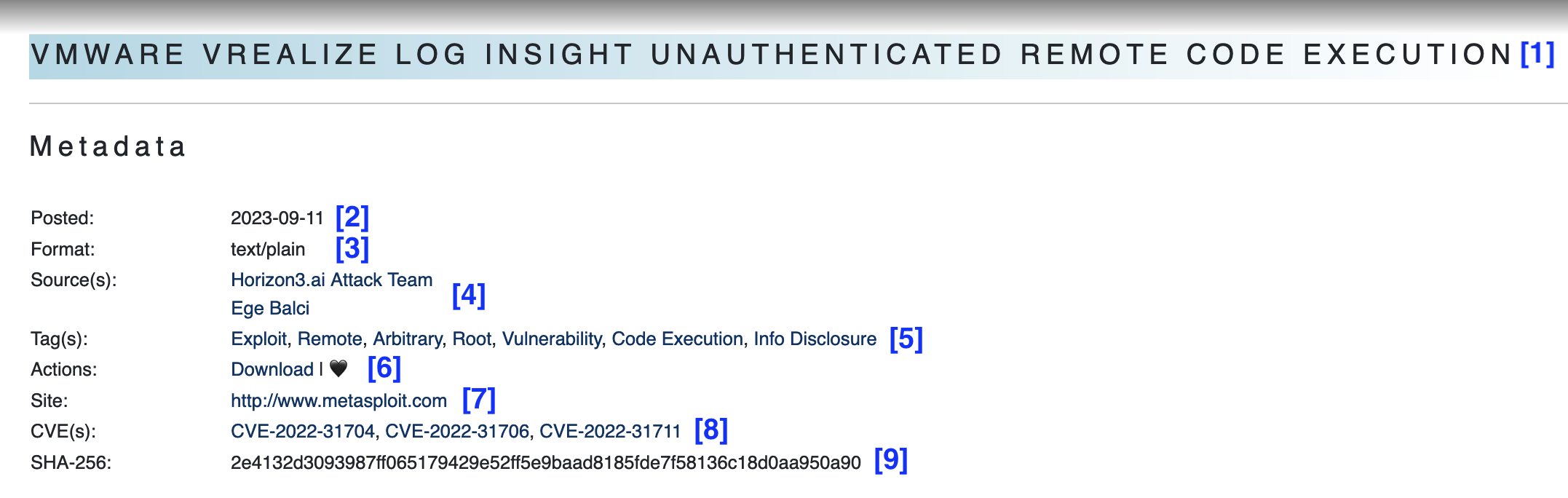



The first line is the title of the entry. For most vulnerability entries, the title will give a very high level summary of the issue and the latest version affected for a given piece of software. In cases where advisories do not provide succinct information, the advisory name and number are provided. Tools are added with their names and their version.
The Posted line notes the date the file was added to the archive.
The Format line notes what format the file is in. If it's not viewable on the page, that means it's not in a text format and may need to be downloaded for further evaluation. Due to tools and various information releases having multiple files, it is common to see .zip and .tgz files on the site.
The Source line notes any and all relevant credits to a given institution or entity. This can be the author of an exploit or a person who contributed to an advisory. Packet Storm makes our best effort to ensure the right credits are provided. Clicking on this link will take you to a page with all related works for the given source.
The Tags line provides a list of related tags for a given classification related to the file. If the file discusses Linux, the Linux tag will be there. If it provides exploitation details, the Exploit tag will be in there. Clicking on a tag will provide a full file list of items with that tag.
The Actions line will vary based on your user state. If you are not logged in, you will get a link to download the file. If you are logged in, you will not only get the download link, but a heart icon (🖤) will show up next to the link. If you click the heart icon (🖤), you will see it light up and you will have made a file one of your Favorites (💗). Please note that Favorites can be viewed from your profile, and are considered as public data at all times.
The Site link, if included, is a link to an external web site that is relevant to the given posting. For instance, if it's a call for papers for a conference, we may link to the conference website. If it's a research paper, we may link to the source of truth. These links are an additional bit of telemetry we track in order to direct users to more information.
The CVE line, if included, provides a list of CVE information relevant to the given entry. Packet Storm is commonly referred to in CVEs and we frequently update our entries to match the mappings on the CVE entry itself. Clicking on a CVE number listed here will take you to a page listing all files in the archive that are tagged with the CVE number, along with providing a description to the issue. This is extremely useful when tracking high-profile issues where the flow of data is coming from many places.
The SHA-256 line is simply a cryptographic checksum of the data itself. If a tool or some other bit of data has been out of your control since you last touched it, you can generate a SHA-256 checksum against the data and compare it to the site to ensure your copy has not been subject to tampering.
Help Section



